In rapidly evolving digital landscape, cloud computing has become an integral part of business operations. However, with great power comes great responsibility, especially when it comes to securing your valuable digital assets. This comprehensive guide will explore the critical aspects of cloud security mastery, providing you with the knowledge and strategies needed to safeguard your organization’s data and infrastructure.
Understanding Cloud Security Challenges
The shift to cloud computing has brought numerous benefits, including scalability, cost-efficiency, and improved collaboration. However, it has also introduced new security challenges that organizations must address to protect their sensitive information and maintain compliance with industry regulations.
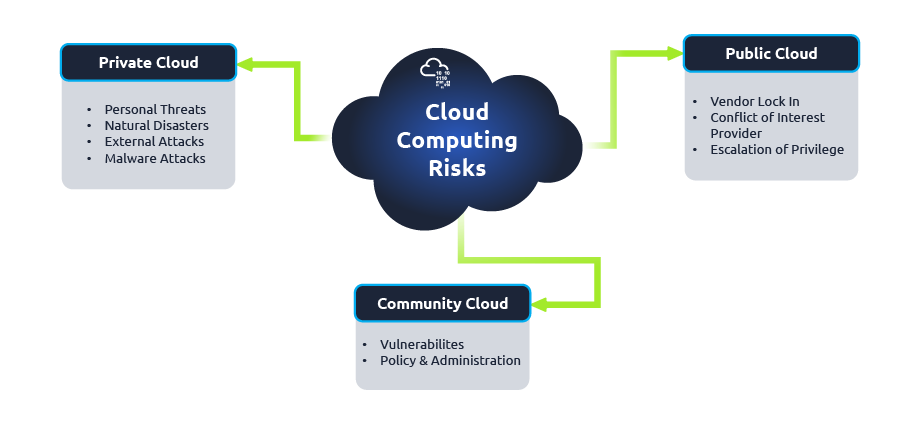
Some of the key challenges in cloud security include:
- Data breaches
- Insider threats
- Misconfiguration of cloud services
- Compliance and regulatory issues
- Lack of visibility and control
Understanding these challenges is the first step towards developing a robust cloud security strategy. Let’s delve deeper into each of these areas and explore effective solutions.
Data Encryption: The First Line of Defense
Data encryption is a fundamental aspect of cloud security mastery. It ensures that even if unauthorized parties gain access to your data, they cannot decipher its contents without the encryption key.
Best Practices for Data Encryption:
- Implement end-to-end encryption: Secure data both in transit and at rest.
- Use strong encryption algorithms: Opt for industry-standard encryption methods like AES-256.
- Manage encryption keys securely: Implement a robust key management system to protect your encryption keys.
- Regularly rotate encryption keys: Change keys periodically to minimize the impact of potential breaches.
By implementing these practices, you create a formidable barrier against data breaches and unauthorized access.
Identity and Access Management (IAM): Controlling the Gates
Effective Identity and Access Management (IAM) is crucial for maintaining control over who can access your cloud resources and what they can do with that access.
Key Components of a Strong IAM Strategy:
- Multi-factor authentication (MFA): Require multiple forms of verification for user logins.
- Role-based access control (RBAC): Assign permissions based on job roles and responsibilities.
- Single sign-on (SSO): Streamline user access while maintaining security.
- Regular access reviews: Periodically audit and update user permissions.
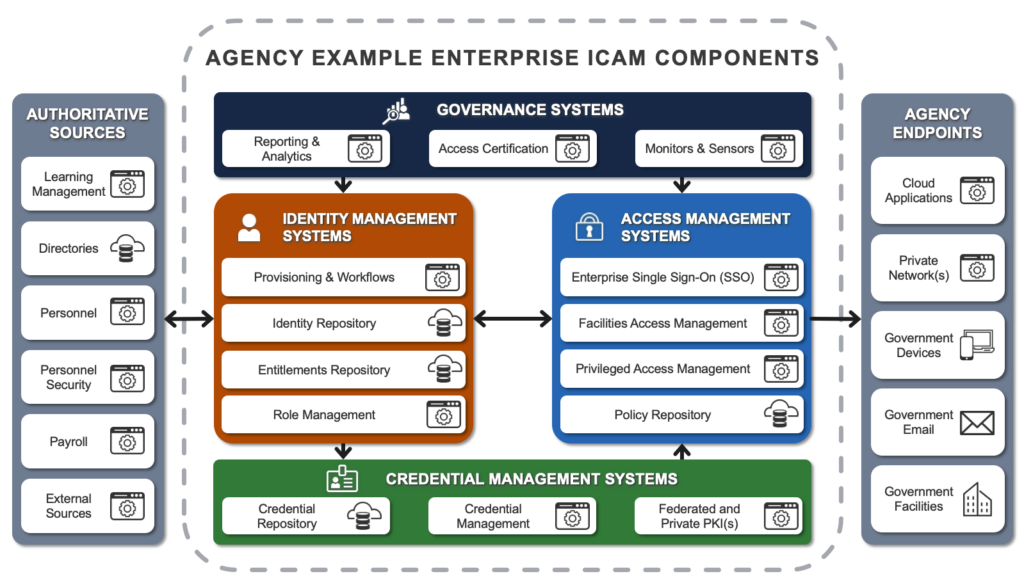
Implementing a comprehensive IAM strategy helps prevent unauthorized access and reduces the risk of insider threats.
Cloud Configuration Management: Avoiding Misconfigurations
Misconfigurations are one of the leading causes of cloud security incidents. Proper cloud configuration management is essential for maintaining a secure cloud environment.
Best Practices for Cloud Configuration:
- Use configuration management tools: Automate and standardize configurations across your cloud infrastructure.
- Implement least privilege principle: Grant only the minimum necessary permissions for each user or service.
- Regularly audit configurations: Conduct periodic reviews to identify and rectify misconfigurations.
- Leverage cloud-native security tools: Utilize built-in security features provided by your cloud service provider.
By following these practices, you can significantly reduce the risk of security vulnerabilities caused by misconfigurations.
Compliance and Regulatory Adherence
Maintaining compliance with industry regulations is a critical aspect of cloud security mastery. Different industries have specific requirements for data protection and privacy.
Steps to Ensure Compliance:
- Understand relevant regulations: Identify which regulations apply to your organization (e.g., GDPR, HIPAA, PCI DSS).
- Implement necessary controls: Deploy security measures that align with regulatory requirements.
- Conduct regular audits: Perform internal and external audits to verify compliance.
- Document everything: Maintain detailed records of your compliance efforts and security measures.
Staying compliant not only helps avoid legal issues but also enhances your overall security posture.
Continuous Monitoring and Threat Detection
In the ever-changing landscape of cyber threats, continuous monitoring and threat detection are essential components of cloud security mastery.
Implementing Effective Monitoring:
- Deploy intrusion detection systems (IDS): Identify potential security breaches in real-time.
- Use security information and event management (SIEM) tools: Aggregate and analyze security data from multiple sources.
- Implement anomaly detection: Leverage AI and machine learning to identify unusual patterns or behaviors.
- Conduct regular vulnerability assessments: Proactively identify and address security weaknesses.
By maintaining vigilant monitoring, you can detect and respond to threats quickly, minimizing potential damage.
Incident Response and Disaster Recovery
Even with robust preventive measures, it’s crucial to have a solid incident response and disaster recovery plan in place.
Key Elements of an Effective Plan:
- Define clear roles and responsibilities: Ensure everyone knows their part in the response process.
- Establish communication protocols: Define how information will be shared during an incident.
- Conduct regular drills: Practice your response plan to identify areas for improvement.
- Implement automated backups: Ensure critical data can be restored quickly in case of a disaster.
A well-prepared incident response plan can significantly reduce the impact of a security breach and help maintain business continuity.
Employee Training and Security Awareness
Human error remains one of the biggest security risks in any organization. Comprehensive employee training and fostering a culture of security awareness are crucial for cloud security mastery.
Effective Training Strategies:
- Regular security awareness programs: Conduct ongoing training sessions to keep security top-of-mind.
- Simulated phishing exercises: Test and improve employees’ ability to recognize and report phishing attempts.
- Clear security policies: Develop and communicate easy-to-understand security guidelines.
- Encourage reporting: Create a supportive environment where employees feel comfortable reporting potential security issues.
By empowering your employees with knowledge and fostering a security-conscious culture, you create a human firewall that complements your technical security measures.
Leveraging AI and Machine Learning for Enhanced Security
As cyber threats become more sophisticated, leveraging artificial intelligence (AI) and machine learning (ML) can provide a significant advantage in cloud security mastery.
Applications of AI and ML in Cloud Security:
- Automated threat detection: Identify and respond to threats faster than human analysts.
- Behavioral analysis: Detect anomalies in user and system behaviors that may indicate a security threat.
- Predictive security: Anticipate potential vulnerabilities and proactively address them.
- Intelligent automation: Streamline security operations and reduce the burden on human analysts.
By harnessing the power of AI and ML, organizations can stay ahead of evolving threats and maintain a robust security posture.
Conclusion
Cloud security mastery is an ongoing journey that requires a multi-faceted approach. By implementing strong data encryption, effective IAM strategies, proper configuration management, and leveraging advanced technologies like AI and ML, organizations can significantly enhance their cloud security posture. Remember, security is not a one-time effort but a continuous process of improvement and adaptation.
Are you ready to take your cloud security to the next level? At Aiblux, we specialize in providing client-centric software solutions that prioritize security and innovation. Our team of experts can help you navigate the complex landscape of cloud security and implement tailored strategies to protect your digital assets. Contact us today to explore how we can fortify your cloud infrastructure and give you peace of mind in an increasingly digital world.
